Security is one of the prominent aspects of Digital Infrastructure.
Keeping this in mind, Two Factor Authentication has been developed to add an extra layer of security at the cloud services level.
Here, we are going to elaborate on how we can integrate Two Factor Authentication in EC2 for SSH using Duo.
Prerequisites:
- AWS Account
- Duo Account
- Installed Duo on Android phone
- Pre-launched EC2 machine with any flavor of Unix
Note: We will use a free trial of Duo
https://signup.duo.com/
Once the “Sign Up” is completed, there will be verification mail in your inbox.
Just verify it.

After verification, there will be a QR code as given below:
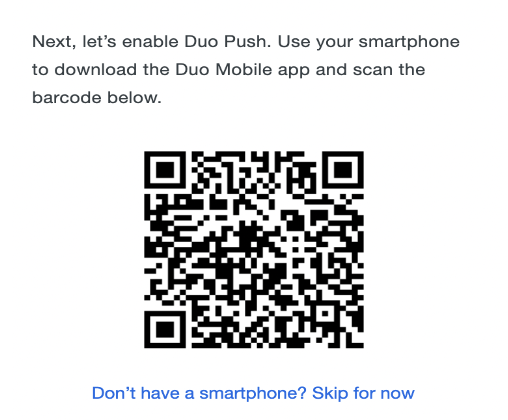
Open the Duo App and scan this QR, and it will be logged in to the web page, and the following page will appear on the web screen.
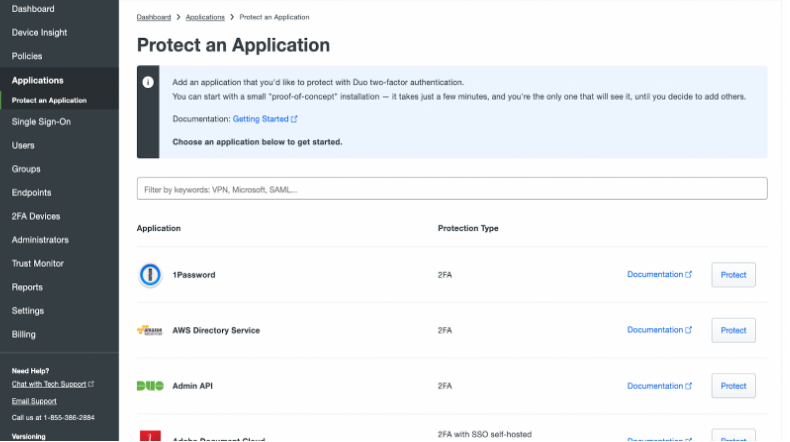
Login to the account and navigate to the Applications section.
Navigate to the search bar under Protect an Application and type ‘Unix Application’.
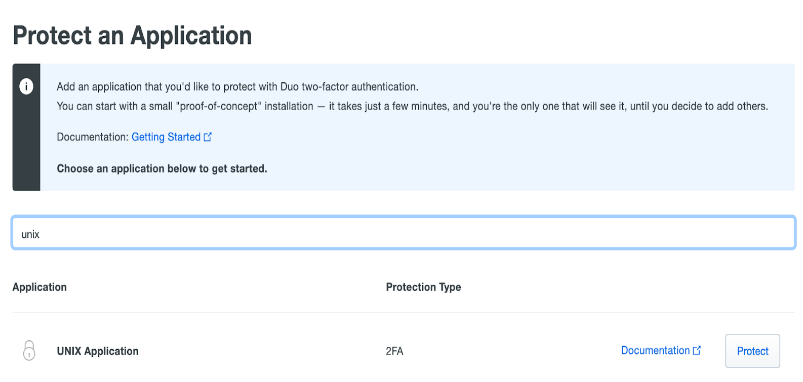
Now click on the Protect button and collect the following information.
The Integration Key, Secret Key, and Host Key as given below:

SSH into EC2 machine
sudo yum update -y
sudo yum install openssl-devel -y
wget https://dl.duosecurity.com/duo_unix-1.11.5.tar.gz
tar zxf duo_unix-1.11.5.tar.gz
cd duo_unix-1.11.5
sudo yum install gcc -y
bash configure --prefix=/usr && make && sudo make install
sudo nano /etc/duo/login_duo.conf
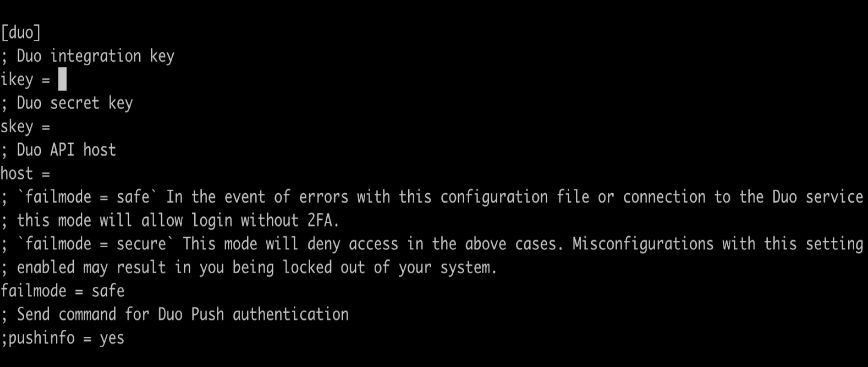
Replace the following values and save the files.
[duo]
ikey=DIXXXXXXXXXXXXXXXXXX
skey=X1hXztPX1rb1X71x1wXkpnmXXvqXXXqqj9
host=api-xxxxxxxx.duosecurity.com
How to Test the Setup
The manual test can be done by executing the following cmd:
$ /usr/sbin/login_duo
If the setup has been done correctly and the username does not exist in your duo, you will get one hyperlink.
Please Enroll at https://api-xxxxxxx.duosecurity.com/portal?code=XXXXXXXXXXX&akey=XXXXXXXXXX
Visit the URL in a web browser, enroll your phone, and then try login_duo again, this time adding a command to run after authentication is complete.
Here, execute the following cmd:
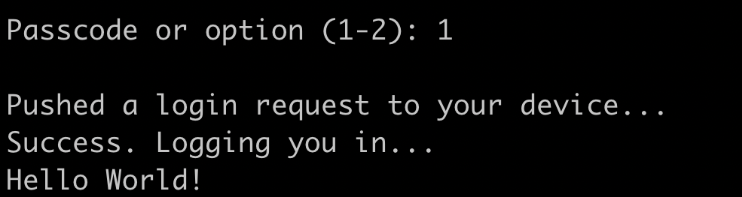
[ec2-user@ip-172-31-42-247 ~]$ /usr/sbin/login_duo echo 'Hello World!'
You should see something like this:

Select 1, and one green tap will appear in the Duo mobile app.
Once you approve the duo login, there will be the following message in EC2:
Enable login_duo
To protect remote access via SSH, use login_duo.
To enable two-factor authentication for any SSH login method (password, pubkey, etc.) for any user, edit your sshd_config.
$ sudo nano /etc/ssh/sshd_config
Add the following line:
ForceCommand /usr/sbin/login_duo
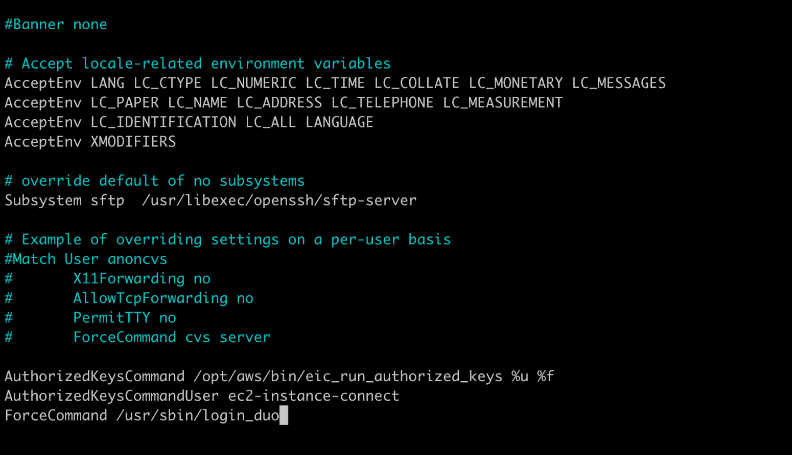
This ForceCommand directive instructs sshd to run login_duo (to perform two-factor authentication) before any other requested commands.
However, according to the sshd documentation: “The command is invoked by using the user’s login shell with the -c option.”
This means that shell rc files (e.g. .bashrc, .cshrc, etc.) execute before login_duo; if users can edit these files, they may be able to disable Duo authentication for their own accounts. Keep in mind that ForceCommand also disables command=. Mitigate these issues by deploying pam_duo instead of login_duo.
We strongly recommend that you disable PermitTunnel and AllowTcpForwarding in your sshd_config when using login_duo to protect SSH logins. Since OpenSSH sets up port forwarding and tunneling before Duo’s two-factor challenge, an attacker may be able to access internal services via port forwarding before completing secondary authentication. Adding the following lines to your sshd_config will prevent this scenario:
PermitTunnel no
AllowTcpForwarding no
[ec2-user@ip-172-31-42-247 ~]$ sudo service sshd restart
Redirecting to /bin/systemctl restart sshd.service.
$ ssh -i duo-test.pem ec2-user@MACHINE_IP

Select 1, and open your Duo app on mobile and approve.
Now it will be logged in.
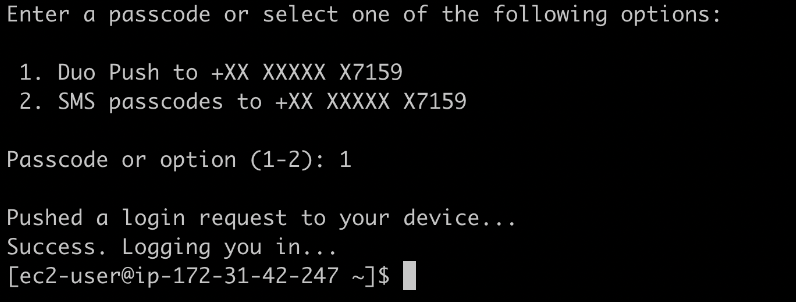
If you want to perform auto-push:
$ sudo nano /etc/ssh/sshd_config

Restart the sshd with cmd.
$ sudo service ssh restart
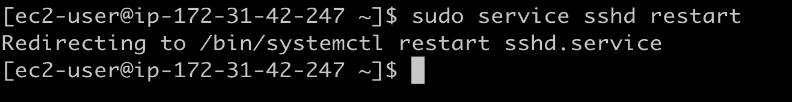
Exit from the machine and perform SSH login in the machine, you will get approval by tapping in the Duo mobile app.
Once you are approved, you will be logged in.
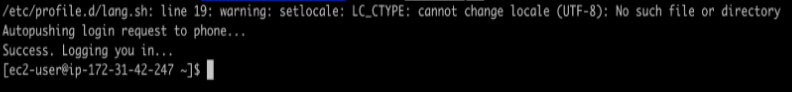
So, this is an example of MFA integration at the machine level.
Use Case of Duo:
- Add an extra layer of security for the AWS account.
- Add an extra layer of security for the bastion host.
Conclusion:
We hope that the two-factor authentication in AWS EC2 for SSH using the Duo mobile app has become easier to deal with now. You can just follow the steps as mentioned above and it will be a walk-on cake. Visit CloudZenia for more such blogs and practical solutions, and learn even about multi-factor authentication.




Leave a Reply