
Introduction to NACLs
Network Access Control List is the additional layer of security for our AWS instances; it acts as a virtual firewall for the instances. It is like the bouncers at the party entrance who decide who gets in and who stays out.

NACL works on the subnet level and regulates the communication between the instances and the outside world. By default, NACL allows both inbound and outbound traffic, working on an ANY-ANY rule; we need to define the inbound and the outbound traffic that NACL has to allow and restrict. As the NACL works on the subnet level, we can have more control over the network.
Purpose of NACLs in AWS Networking
- Granular Control – Via NACL, we can maintain finely-grained control over the traffic that is entering and leaving the subnets. We can define rules, types, protocol, port range, etc., and get granular control over the inbound and the outbound traffic.
- Strong Defense – Each subnet must be associated with an NACL that ensures a strong defence at the subnet level. Having a layer of security at the subnet level blocks any false request before entering our instances.
- Stateless Filtering – NACLs are stateless (we will look into this more deeply later), meaning they don’t remember the past traffic, and each packet is evaluated independently.
What is Stateful and Stateless?
- Stateless
When a network packet enters the network subnet, each packet is treated independently without any memory of the past packets, which makes NACL stateless.
- Let’s understand it with a real-life example – suppose you were to attend a party where the bouncer remembers everyone who enters and then forgets about them. When a guest arrives (inbound traffic), the bouncer checks their name, ID, ticket, etc., and if the ticket says allowed, they allow them, but the bouncer doesn’t remember them once after.
- Now, when a guest leaves (outbound traffic), they need a separate ticket to get out of the party. Here, in the case of our analogy, the bouncer doesn’t automatically know that if a guest comes, they are allowed to leave as well. The guest leaving must have an extra set of permission to get out of the party.
- If you understood the example well, NACL is your bouncer, and with certain sets of permissions, it lets the network enter inside the subnet. It also requires some extra rules to let that network packet leave the subnet. For this reason, NACL is stateless.
- How does Stateless NACL work?
– We need to set inbound and outbound rules to specify which traffic is allowed to enter and which is allowed to exit. When the rules for access control in network security are set, they are assigned some numbers. These rules are evaluated sequentially (from the lowest to the highest rule number).
– If a rule matches, it’s applied, and no further evaluation occurs.
Using this property of NACL, we can increase the security of our infrastructure by working on the subnet level. We can associate a single NACL with multiple subnets, but each subnet can only be associated with a single NACL at a time.
Examples – You create an inbound rule to allow HTTP traffic (port 80) into your subnet. But responses to that HTTP traffic (outbound) aren’t automatically allowed; you would have to allow both inbound and outbound traffic into your subnet.
- Stateful
In the case of Stateful, the scenario is the opposite. In Stateless, the state is saved, so we do not have to specify both inbound and outbound rules separately, but if we want, we can set them. A good example of stateful is Security Group.- Let’s take our party example again and try to understand, this time the bouncer recognizes once you have verified yourself at the time of entering the party and allows you to leave the party without asking for your identity.
Example – When you create a security group and set some inbound rule, let’s say for HTTP(80), you do not need to specify an outbound rule; the stateful property of the security group will automatically allow the outbound traffic.
NACL Rules Fields
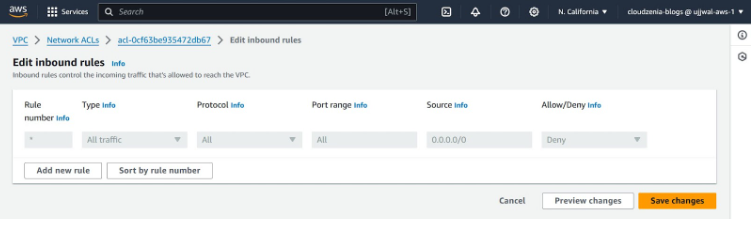
Let’s understand different fields while creating AWS Network Access Control Lists-
- Rule Number – Each rule in NACL is assigned a unique rule number. These numbers can range from 1 to 32766 – the lower the number, the higher the priority.
When traffic enters or leaves the subnet, NACL rules are evaluated, and according to these rule numbers, evaluation of the rules occurs, and as soon as the rule is matched to the traffic, it defines the action (allow/deny). - Type – It is the type of traffic your rules are applied to like HTTP, HTTPS, SSH, etc.
- Protocol – It is the network protocol associated with the rule, for example, TCP or UDP.
- Port Range – It is the range for the ports that you want to allow or deny your traffic.
- Source – It defines the source of the traffic and can be either IP Address, CIDR block, etc.
- Allow/Deny – Whether you want to allow or deny the traffic with a certain rule.
Conclusion
NACL is one of the best practices that you should follow to secure your infrastructure. We hope this blog helped you understand the concept behind Network Access Control List AWS, and also, now, you can clearly understand the difference between stateful and stateless. Using the rule number, you can even set the priorities for your rules. Overall, you should use NACL to protect your infrastructure at the subnet level in AWS.
Thank you for reading the blog!
You can visit our website, CloudZenia, for more informational and technological blogs.


