Introduction
Configuration management is critical in managing various types of servers, maintaining their state, patching them regularly, and protecting them with updated security patches. We need automation for a variety of other tasks. Consider how configuration management may help us automate repetitive processes. For example, if there are ten servers where you need to create certain users or install specific services, doing this one by one takes a long time. Here, configuration management comes into play.
Numerous tools exist in this domain, including Ansible, Chef, Puppet, and Salt. The Ansible tool is more popular and widely used for configuration. Red Hat developed Ansible and maintains it. This blog will discuss Ansible and configuration management to manage servers.
Prerequisite
- Three EC2 servers.
- Understanding of Linux and its commands.
Step-01: Setup the servers
- Launch Three EC2 (ubuntu) instances.
- Name it as Controller, Agent-1 and Agent-2.
- Install Ansible on the Controller instance using the below commands,
sudo apt update
sudo apt install ansible
ansible --versionNote: The managed node (the machine that Ansible manages) does not require Ansible to be installed but requires Python to run Ansible-generated Python code. The managed node also requires a user account that can connect through SSH with an interactive POSIX shell to the node.
Step-02: Established password-less SSH
- passwords of agent servers repeatedly.
- Generate SSH keys on the Controller server.
ssh-keygen- The above command generates a public and private key stored in path ~/.ssh, i.e. the directory inside the user’s home directory.
- Copy the public key and paste it into the agent servers inside the ~/.ssh/authorized_keys directory.
- Modify the sshd_config files; the attributes below need to be changed.
PubkeyAuthentication yes
PasswordAuthentication no
AuthorizedKeysFile .ssh/authorized_keys- Verify your SSH does not need a password from the Controller server,
ssh user@slave_host- Checkout the video below for a better understanding
- Do the same for other servers as well (slave-2)
Step-03: Create an inventory file and a playbook
- Inventory (hosts): It is a simple text file (.txt) in which we specify server IPs or groups of IPs to run the automated script on this server; Ansible checks this file while running the playbook as hosts form a crucial component of the architecture.
- Playbook: Another important component of the Ansible architecture is the playbook which is a set instruction file written in yaml; we mentioned all the steps that need to be performed on agent servers; here, the important ones are Modules. There are many modules available in Ansible. You can use this to automate your task according to requirements. You can also write your modules using Python.
- Once you install Ansible successfully, let us create the above files. Make one directory named Ansible and create two files,
- In setup, you can relate hosts as an inventory file and webserver.yml as a playbook.
mkdir ansible
cd ansible
touch hosts webserver.yml- Please copy the below content and paste it into the respective files,
hosts
[webservers]
slave-1-public-ip
slave-2-public-ipwebserver.yml
---
- name: Ensure Apache is installed and running
hosts: webservers
become: yes # Use sudo to perform tasks requiring elevated privileges
tasks:
- name: Update apt cache
apt:
update_cache: yes
- name: Install Apache
apt:
name: apache2
state: present
- name: Ensure Apache is started and enabled on boot
systemd:
name: apache2
state: started
enabled: yes
- name: Create a custom index.html file
copy:
dest: /var/www/html/index.html
content: |
<html>
<head>
<title>Welcome to Ansible Managed Web Server</title>
</head>
<body>
<h1>Success! The Apache server is installed and running.</h1>
</body>
</html>Step-04: Run the playbook
- We already set up the passwordless SSH, and now we can proceed with running the playbook.
cd ansible/
ansible-playbook -i hosts webserver.yml- After the playbook has successfully run, your servers are converted to web servers hosting simple web pages.
- Checkout below video for ease
Step-05: Verify the changes
- Now, copy the public IP of any of the agent servers and try to access them. You will set the URL below.
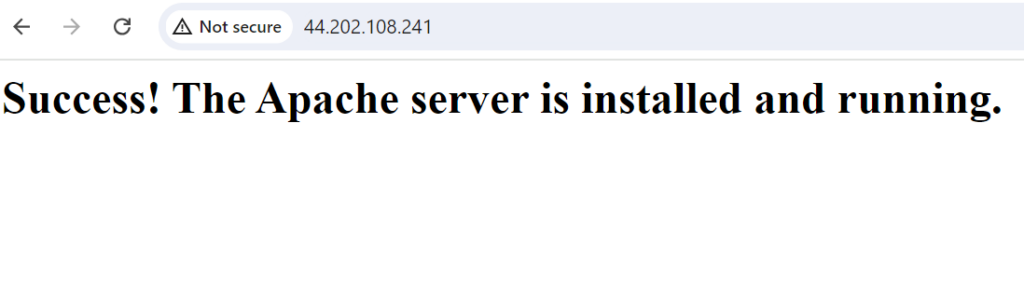
Conclusion
In this blog, we discussed Ansible, how it works, and how to configure it. This has several learning curves, so I recommend reading material and experimenting with various scenarios. Also, comprehend the modules to use Ansible feasibly. The more modules you have, the more adept you are using Ansible.
For more details and complete information on Ansible, cloud computing, configuration management, and cloud technology, visit the CloudZenia website.
Happy learning.


